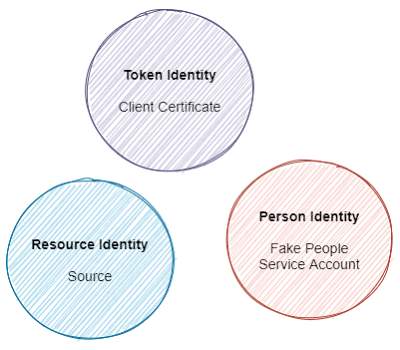
Demonstrating creating EventHubs and Identities using the Azure template engine
Create resources in Azure using the Azure Portal Template UI. We created a resource group with a Namespace and individual EventHubs in another video. Then I exported the resource group contents to a JSON file. Here we load that JSON file into another Resource Group to recreate the EventHubs and their associated identities and security settings. The code for this discussion came out of working on a different blog posting . The exported template is mostly hardcoded. You will want to parameterize any names that might vary by environment by reuse of the template for other purposes.