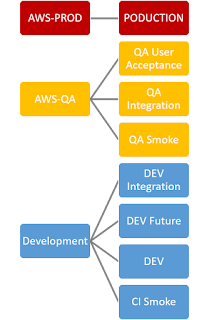
A Chrome Plugin: IsItUp serverless service dashboard

A coworker created a Chrome Extension that acts as a zero-infrastructure dashboard. It provides a simple home page that displays service health and support or documentation links related to that service. The plugin reads JSON file/text to make service calls and build the dashboard. The following picture shows 5 services across up to 6 environments. The top service does not have a Production environment. The bottom service represents a 3rd external service that has one test environment and one production environment. The IsItUp chrome executes health checks via HTTP/HTTPS calls. The extension requires connectivity to the services being monitored. Video Walk-through The video explains various cell examples and describes how the extension might be used. The plugin used for the video was downloaded from the Chrome Web Store . Video created with version available Jan 21 2017 Cell Explanation Each cell contains one Service Status plu...