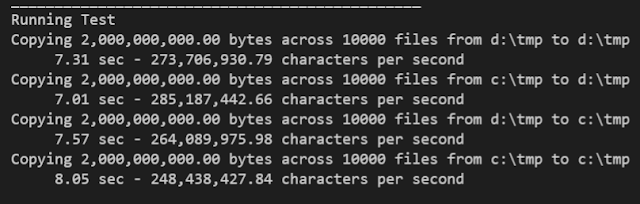
Quality is day 2 - the day that never comes
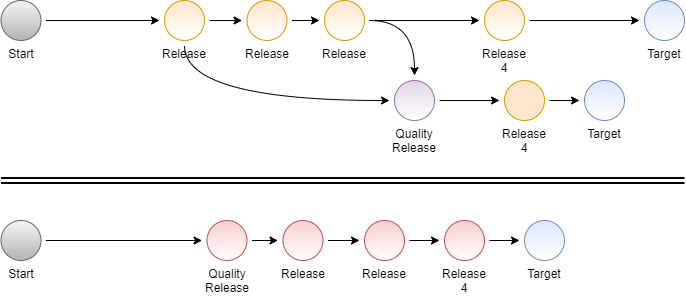
Quality has to be baked into the decision-making process from the beginning of any effort. We often talk a good game about making sure we improve the quality of a product or process at "some time in the future" or "in the 2nd release". We hear this a lot in the crunch period at the end of a project. The date or some features trump repeatable process or quality efforts. The next iteration is filled with "must-have features". Day 2 turns out to always be the next release, next quarter, or never. Baking corner cutting into the process Some groups just own that they will produce junk and build stabilization sprints and quality increments into their process. They schedule specific periods for additional testing and QC. I've seen this work and I've seen it become a major anti-pattern where teams get even sloppier because they know there is a quality improvement phase. Immediate payof...