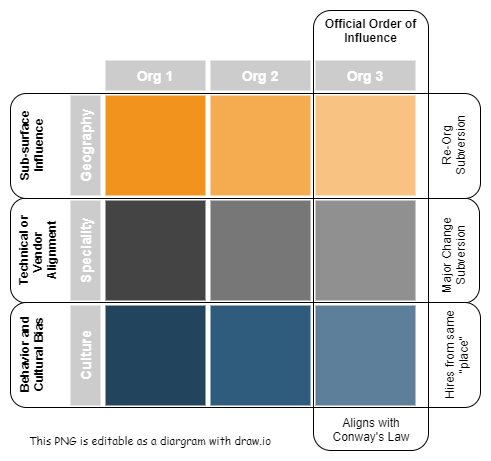
My Wi-Fi is slow. Is it really the Wi-Fi?
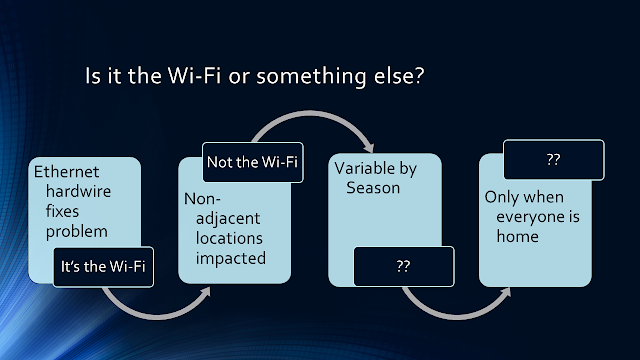
How do your devices connect to the Internet? How does that connection get to the information super-highway? The only way to know is to have some general understanding of how a connected device gets to the remote web site or service. ISP service levels are sold at performance levels, bits per second. That does not guarantee you that level of performance from your mobile devices all the way to your internet services. Your network configuration combined with your neighbors and your ISP configuration can have a real impact on your effective throughput. People often say their wi-fi is slow when they talk about their internet experience. Do they really mean it is wi-fi or the internet or somewhere in between? We talked to someone in a beach neighborhood during the summer and they complained that their wi-fi was Slow . They then said that a lot of neighbors had wi-fi problems. These were single-family homes far enough apart that wi-fi may not...