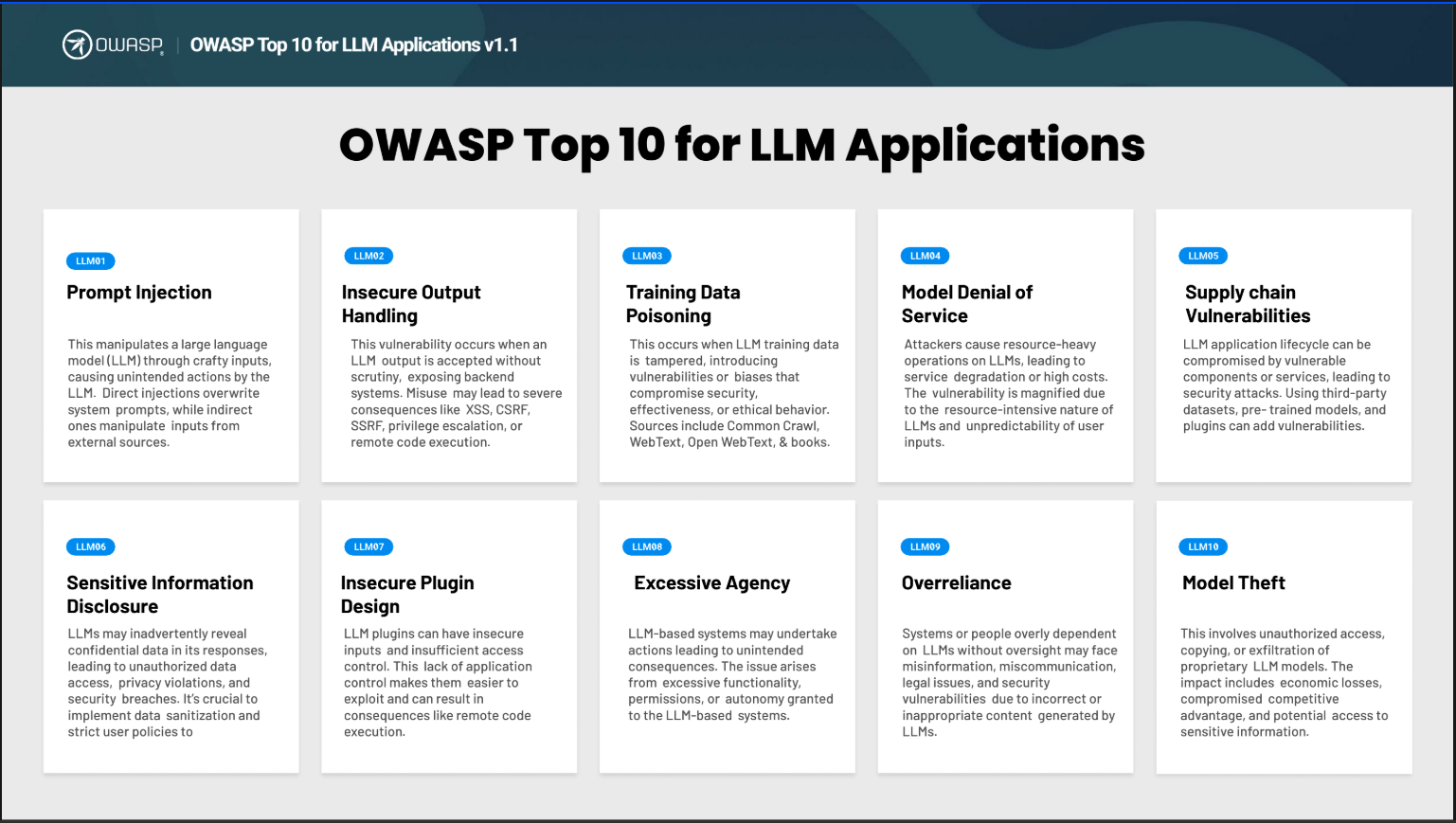
The hot ticket right now is "Put AI Everywhere". This usually results in a race to come up with ideas about how AI can be used in new products or existing systems. I suggest creating a system to analyze existing processes, software, and programs with a structured approach, identifying opportunities and assessing risks and rewards. LLM agents, chat bots and instructors models that turn human speech and writing patterns into content or actions is in scope here. TTS, STT, translators and other non integrated LLM uses are out of scope. The talk below iteratively breaks down our process until we reach the point where we identify AI opportunities. We start with PDCA (Plan-Do-Check-Adjust) as a notion for the lifecycle of products, software, and processes. We can map that into the following in the software space. Item 4 could be anything specific to your domain. Design Time: All of the processes that happen before actual code execution. This is before transactions, customer ...