2025 OWASP Top 10 for LLM Applications - Creating a common understanding of security risks
LLM-supported AI is being stuffed into every computer-based and computer-assisted process. A lot is being said about the benefits of LLM, with some secondary discussions about security and behavioral risks. Many of the risk discussions have been unstructured bullet points or anecdotal stories of hacked systems. The OWASP Top 10 for LLM Applications 2025 provides a framework for understanding the top risks of an LLM-integrated system. The OWASP Top 10 for LLM Applications deserves the same attention the OWASP Top 10 for Web applications has held for over a decade.
The Developer's Playbook for Large Language Model Security by Steve Wilson provides a solid foundation for understanding risks existing in an LLM ecosystem. It also led me to the OWASP Top 10 for LLM Applications 2025. This is a great resource for anyone looking to integrate LLMS into business processes or existing systems. I got this book as part of a set of O'Reilly books in a Humble Bundle.
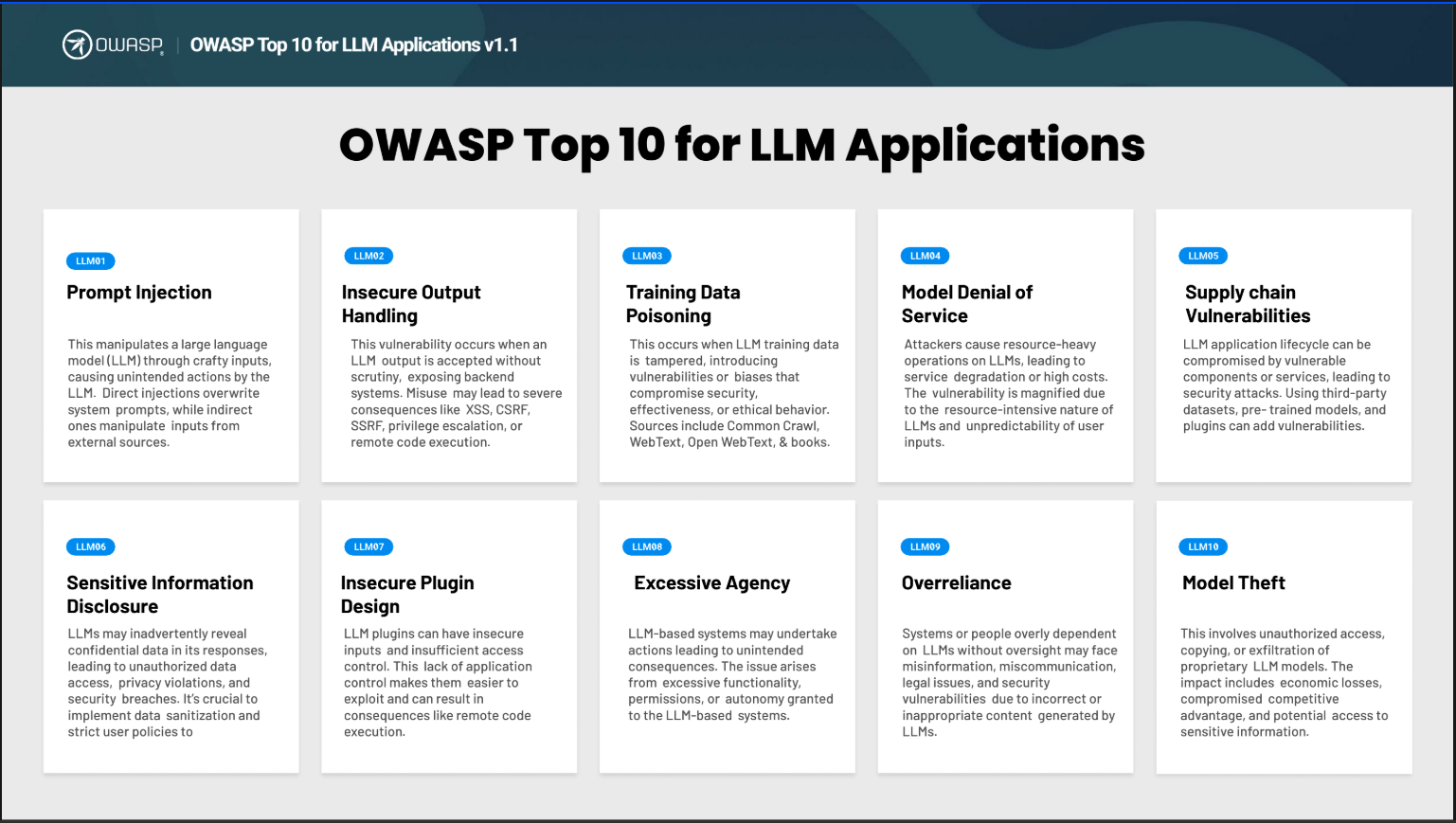
OWASP Top 10 for LLM Applications v1.1
- LLM01 Prompt Injection
- LLM02 Insecure Output Handling
- LLM03 Training Data Poisoning
- LLM04 Model Denial of Service
- LLM05 Supply Chain Vulnerabilities
- LLM06 Sensitive Information Disclosure
- LLM07 Insecure Plugin Design
- LLM08 Excessive Agency
- LLM09 Overreliance
- LLM10 Model Theft




Comments
Post a Comment