Cloud Native and other Identities in Azure
Moving into the public cloud involves balancing known techniques against cloud-native approaches. Identity management and Authentication/Authorization is one of the areas where you can use your legacy on-prem approach or a more cloud-native approach.
Managed Identities are a powerful cloud-native identity available in Azure. They are integrated at the Azure resource level, providing identities without the hassle of secrets management or separate lifecycle processes. Managed Identities can act as a logical replacement firewall in cloud-only resource-to-resource topologies.
Identity Types
We are going to talk about 3 styles to cloud identity.
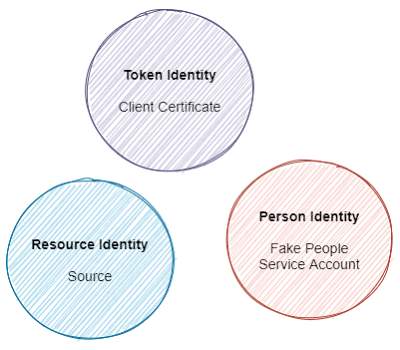
- Person Identity: A user account, traditionally secured with a username and password. User accounts are common in many systems. Applications will often use a fake person or service account as their identity. Service account credentials, passwords, must be protected and rotated. This type of identity can be passed from one system to another as a token. These are often accepted by 3rd party applications like databases.
- Token or Shared Secret Identity: These exist to support API calls. For the purposes of this discussion, they are bound to the target system. They may be implemented as a signing key and are often created by the receiving system and are bound to a set of privileges. SAS and Tokens must be protected because they are portable bearer credentials. In that sense, they are slightly similar to Client Certificates.
- Resource Identity: These are cloud-native credentials designed for cloud resources. They represent the calling resource, a virtual machine, an application pod, etc. Resource Identities represent the calling resource and not the person the request is being made on behalf of. They are installed into resources and presented by the resource as tokens when calling other resources. Resource Identities disappear when the resources are destroyed. Resource Identities reduce handling burdens as they are not touched by development or ops and are destroyed automatically when the calling resources are de-provisioned. Azure also supports User Assigned Identities that can be assigned to any number of cloud resources. Cloud resources can present their System Identity and any number of User Assigned Identities when making a call.
People and OBO versus System to System
We're talking about the credentials used for system-to-system communication. Human-level permissions will often be integrated into edge applications. Those edge applications then use their system credentials to communicate to data stores and other systems inside the network.
EventHubs Example
Namespace Manage permission is restricted to clients that present Signed Access Secrets. SAS is not the most secure identity protection. It is easy to work with from a CI/CD deployment pipeline and can act as a stand-alone identity. That reduces the incentive of creating some ADO super identity whose credentials could be moved somewhere else. Note that Manage permission requires READ and SUBMIT permissions.
The EventHub at the bottom is protected by Managed Identity restrictions. The K8S cluster is the only Azure resource that can submit events. The Azure Function is the only resource that can read the events. We may wish to block shell access to the K8S pods so that only the application code presents the Identity credentials.
The top and middle EventHub/topic support AWS, probably Azure AD, user credentials. The AD user would be given the standard Azure Event Hub permissions that would be bound to those EventHub. This is not demonstrated in the github repository referenced above.
Video
This blog article was revised after the video was created.
Identity Features
Identity types come with their own advantages and disadvantages. 3rd party and legacy integration often necessitate a hybrid approach with cloud-native credentials internal to the cloud and 3p and AD credentials at the edge.
| Identity Style | Cloud-Native | Bound to Resource | Zero Touch | Auto Delete | Revokable | Is Individ. | 3p Usable | 3p Accept | Can Composite |
|---|---|---|---|---|---|---|---|---|---|
| System Managed Identity | Yes | Yes | Yes | Yes | No | No | No | No | No |
| User Managed Identity | Yes | Yes | Yes | Yes | Yes | No | No | No | Yes |
| Signed Access | No | Yes | No | Yes | Yes | No | Yes | No | No |
| User Principal | No | No | No | No | Yes | Yes | Yes | Yes | No |
Columns
- Cloud-Native
- Bound to Resource
- Zero Touch
- Auto Delete
- Revokable
- Represents an Individual
- Can be used by 3rd party applications
- Is accepted by 3rd party applications
- Can combine multiple credentials of the same type
Created 8/2021




Comments
Post a Comment