Managed Identities and Shared Access Tokens for EventHubs in Azure
Azure EventHubs can be secured via IAM Role Permissions and Resource Access Policies. They each have their own advantages and disadvantages as discussed in a previous blog posting. We can see how the various Authorization techniques come together in the Azure Portal.
GitHub Repository
The Azure portal images in this blog were generated using the 8/2021
version of this Github repository:
Azure EventHubs Example
Example Security Posture
Our sample uses different authorization bindings to suit different client
types. It applies those bindings at different places in the resource
hierarchy.
Individual EventHubs and Namespacesuse
Identity Access Management with a Managed Identity and
Standard Azure Roles for some use cases. They use
Shared Access Policies and signed requests for other use
cases.
Permissions are applied at the Namespace and individual
EventHub levels. Namespace permissions are in
herited by the individual EventHubs. EventHub permission only applies
to individual topics.
Video Walkthrough
In the Portal
We can see our deployed components and permissions in the
Azure Portal
Resource Group
The Resource Group is the root of all Azure resources in this
example. We can see our EventHubs Namespace and a
Managed Identity in the resource group.
Managed Identity
The Managed Identity pane shows all the role assignments for this
identity. It shows the identity-centric view. Our
identity has two Standard Azure resource-bound role
assignments. The identity has Listen and
Submit permissions on the namespace.
Resource Group
We go back to the resource group pane to find the
EventHubs namespace that we created.
EventHubs namespace
Clicking on the namespace takes us to the namespace management pane
which has several views available via the left-hand menu. The sample
code implements two different types of permissions to the
namespace.
- An Identity that is role bound to the namespace with Send and Listen privileges
- A SAS token that is bound to the namespace via a Shared Access Policy with Manage privileges.
EventHubs namespace - IAM
The namespace portal has its own IAM pane. That pane is essentially
the inverse of the Identity view shown above. It presents the
Identities and their roles that
are bound to this namespace. The pane shows that our managed
identity has two role assignments bound to this namespace.
EventHubs namespace - Shared Access Policies
The namespace has a Shared Access Policy that grants
Manage permissions to any caller that signs requests with the
SAS Policy secret. This is a powerful secret that must be
secured.
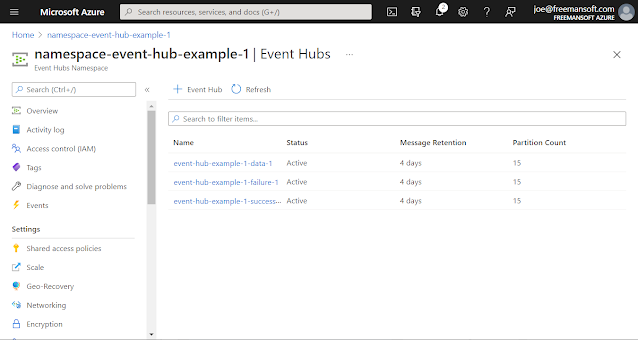
EventHubs in the namespace
There is an EventHub menu item on the left-hand side that you
can't see. It brings up the list of EventHubs in this namespace.
The right-hand pane shows three hubs each with 4-day retention and 15
partitions. The partition count is essentially the level of
parallelism possible with those EventHubs
Individual EventHub - IAM
Thie right-hand pane shows inherited and directly assigned IAM
bindings. It shows all of the identities that have permission to
do work with this individual EventHub. Those permissions could be
directly bound to the individual EventHub or inherited via the
namespace.
Our managed identity that is bound to the namespace shows up
here. The permissions in the picture are inherited from the
namespace. We saw them in one of the namespace views
above.
Individual EventHub - Shared Access Policy.
This EventHub has a shared access policy that lets the SAS
presenter send messages to the EventHub. This lets an entity, that is
not hosted in Azure, send messages to this EventHub. It just needs to
sign the request. The sender could be a 3rd party or a mobile
app.
Deploy the demo code and explore for yourself.
Created 2021 08











Comments
Post a Comment