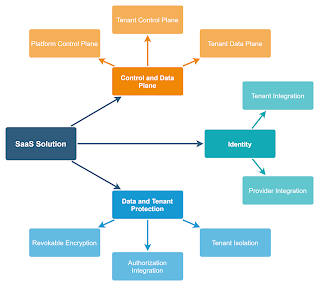
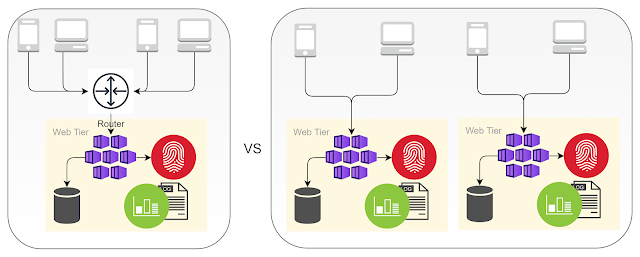
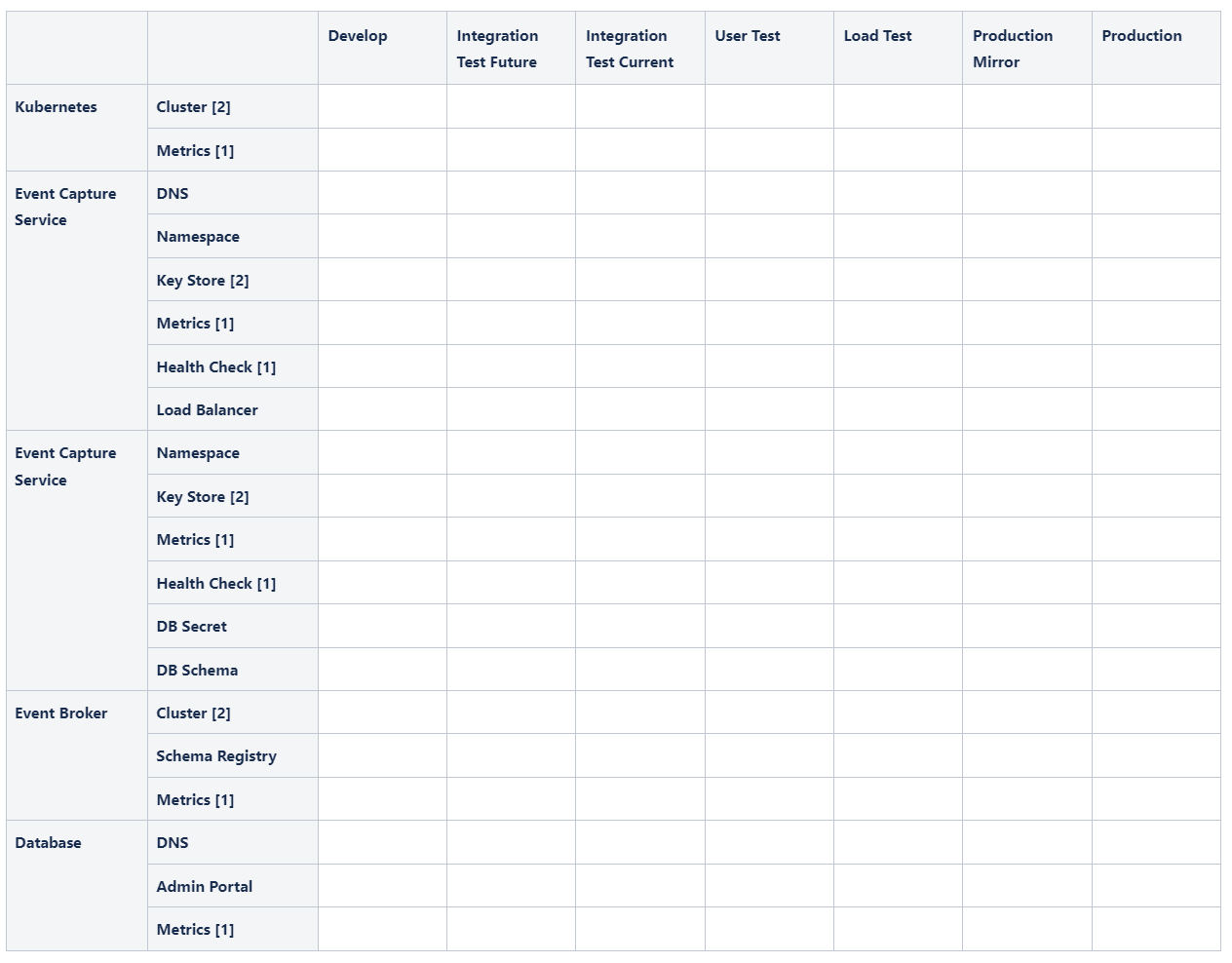
SEP and its evil twin Someone Else's Problem

Someone Else's Problem is a term that declares that some work out of our control or scope. Sometimes we declare someone else's problem so that we don't have to take any action. I n the best situations, we evaluate and declare SEP so that we can focus on our core needs. Maintaining focus and scope control is one of the hardest things to do when creating new software systems or implementing various types of programs. Every decision or new requirement spiders off to touch other requirements that demand other decisions. Some of those touchpoints belong to other teams. This means your success is dependent on the actions of those other teams with other priorities. Sometimes that means you have to get heavily involved with the other team's activities to ensure that they do what you need. This takes focus away from activities that are truly within your charter. SEP as avoidance One o...