Remote work network complexity - VPNs, proxies, split tunnels.
The incredible increase in remote work, continually escalating security concerns, the shift to SaaS providers for office productivity, and exploding bandwidth demands have changed the way companies manage connectivity. Companies are moving from always-on network VPNs to a mix of cloud proxies and zero-trust models.
Home users connect to all services via public internet connections. Corporations typically block this type of access via IP or geo-location blocking that limit access from corporate networks or remote sites.
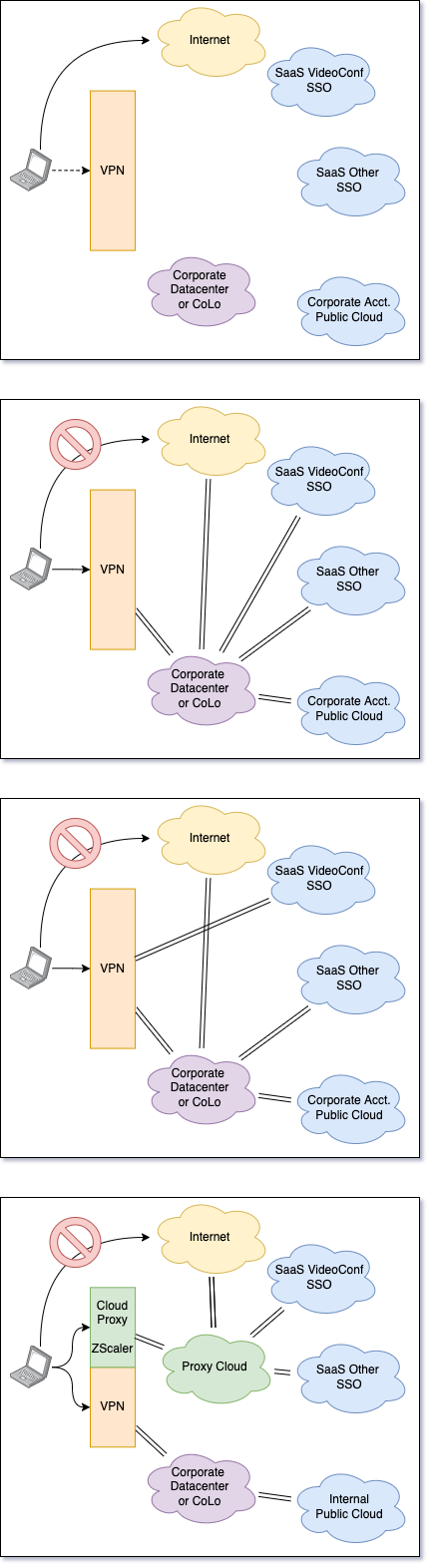 Corporations extended internal hardware and security models by providing remote sites and remote users with corporate-owned machines that join the corporate network via VPN. The VPN bridge the local network to the corporate network. They appear inside the company similar to the way they do inside corporate facilities.
Corporations extended internal hardware and security models by providing remote sites and remote users with corporate-owned machines that join the corporate network via VPN. The VPN bridge the local network to the corporate network. They appear inside the company similar to the way they do inside corporate facilities. This provides all the benefits and risks associated with being inside the network. Remote machine and site breaches give the attacker broad access to corporate networks.
VPNs historically blocked direct access outside the VPN and sent all traffic to the corporate site for inspection. This was done in order to stop bad actors from jumping between the external network and the internal network available on the VPN. Internet and public app traffic was routed to the corporate gateways after which it is then forwarded to the internet. This pushes a lot of network traffic onto the corporate VPN links. It can create bottlenecks for high bandwidth users like video conferencing.
VPNs offer split-tunnel capabilities where specific traffic can be explicitly routed outside of the VPN. This is typically done via IP ranges. Corporate video conferencing often has specific IP addresses to support this. VPN split-tunnel routing treats those addresses as exceptions routing them over the public Internet, off the VPN path. VPN routes are pushed to each remote device or site.
Cloud proxies like ZScalar move on-prem inspection and protection from the private or hybrid-cloud to the proxy provider. VPN tunneling is reconfigured so that all public internet and publicly peered service traffic travels through the cloud proxies. This removes all 3rd party SaaS and internet traffic from the corporate network. Cloud proxies provide their own inspection and access management that is equal to or better than the same features implemented in the data center.
VPNs are typically only needed for internal applications, internal data stores, or processes that require access to resources only routable from the internal network. Many users will be able to work for long periods of time without logging into the corporate VPN.
Presentation
Created 2022 06



Comments
Post a Comment