Remote work network complexity - VPNs, proxies, split tunnels.
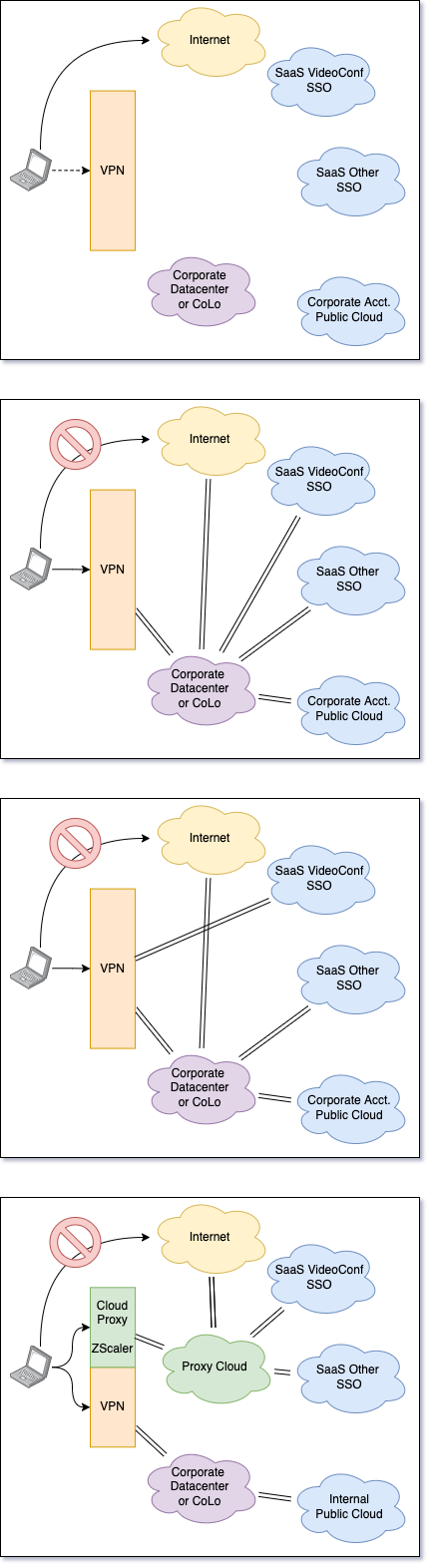
The incredible increase in remote work, continually escalating security concerns, the shift to SaaS providers for office productivity, and exploding bandwidth demands have changed the way companies manage connectivity. Companies are moving from always-on network VPNs to a mix of cloud proxies and zero-trust models. Home users connect to all services via public internet connections. Corporations typically block this type of access via IP or geo-location blocking that limit access from corporate networks or remote sites. Corporations extended internal hardware and security models by providing remote sites and remote users with corporate-owned machines that join the corporate network via VPN. The VPN bridge the local network to the corporate network. They appear inside the company similar to the way they do inside corporate facilities. This provides all the benefits and risks associated with being inside the network. Remote machine and site breaches give the a...



