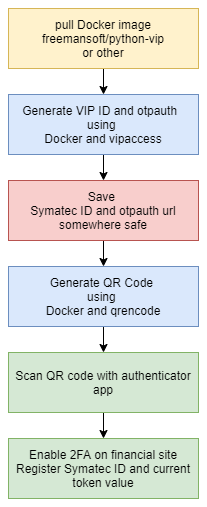
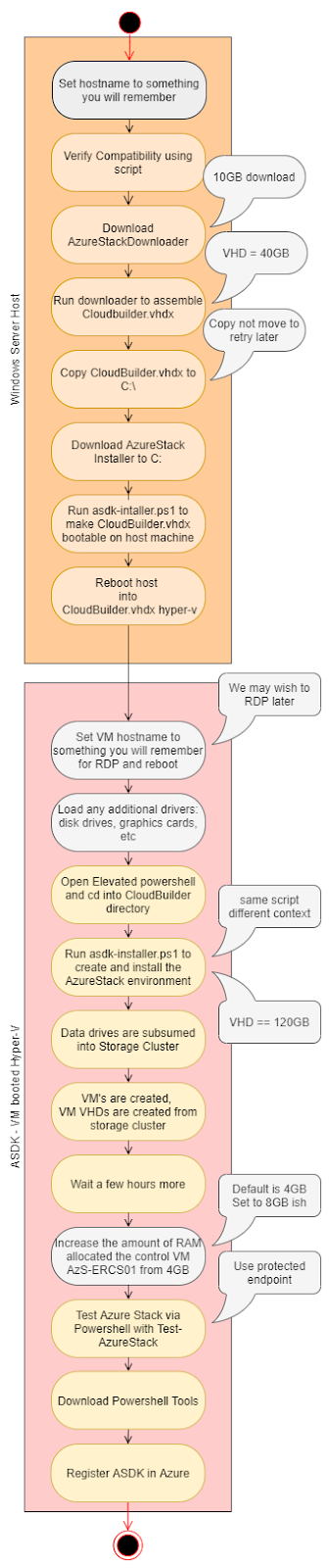
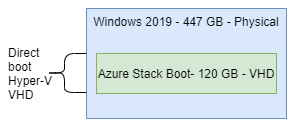
Sales Engineer Guide: Understanding the vendor elimination phase
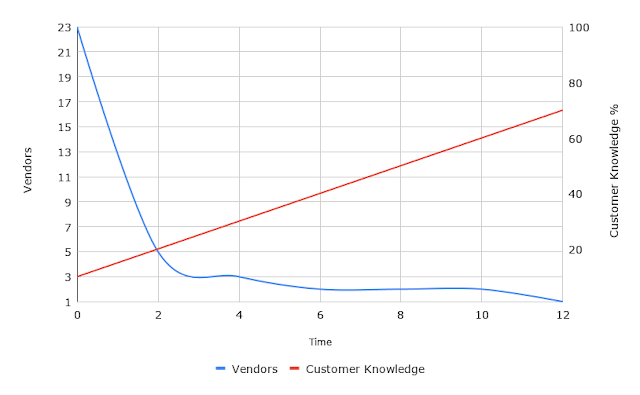
One of the hardest things for technical people to understand is how to adjust answers taking into account context and where the questioner is in their evaluation process. The blue line describes how evaluators eliminating as many options as possible as early as possible. They do this so they can dig deeper into the few options that are left. Evaluators may use in-house analysis or leverage professional research companies . The red line conveys the idea that decision makers learn as they go along. Note that the mass elimination often happens before they truely understand the scope of what they need to know. The customer works to reduce their problem space to something manageable. They start with a Vendor Elimination phase where they try to learn as much as possible while eliminating as many vendors as soon as possible. They ask all kinds of questions to learn more and to eliminate many options quickly. A straight up "no" answer that me...