Creating a No-Patch Security Cadence
A zero-patch environment is one in which we redeploy our applications with updated dependencies as part of our normal Continuous Deployment process. This is part of You Build It - You Own It
We need to create a repeatable cadence for bringing in Operating systems, containers, application patches, and binary updates. We can reduce some of our work by pushing as much of our workload as possible onto PaaS, serverless, and cloud services.
Three Month Cycle Example
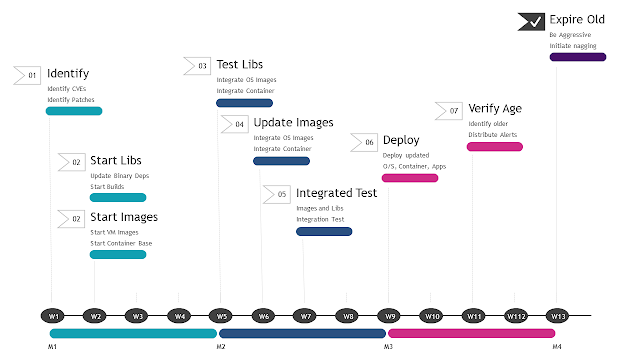
This is a prototypical 3-month update cycle where an application is
redeployed with security and bug fix updates at least every quarter.
|
| Click to enlarge |
- The Image team identifies required operating and container image updates. Application teams identify CVE library updates via automated scanners.
- The application teams start integrating library updates. The image team starts creating new VM and container base images with updated dependencies
- The development team starts testing library and configuration updates
- Images are available. The development team builds applications on new images
- Automated and possibly manual testing is done with the updated binaries and images built on base images.
- Applications are deployed in production
- Compliance tooling starts verifying updates have been done.
- Out of date deployments in non-prod are torn down forcing redeployments
Video
Created to 2022/03



Comments
Post a Comment