Creating Service Accounts for programmatic access to Google Drive APIs
Google Drive is one of those cloud technologies that democratized cloud access to data storage. It lets you securely push all kinds of data into and out of the cloud via Google-provided APIs. APIs and documents are bound to permissions, roles, and identities. Programs accessing Google Docs require credentials, preferably least-privilege credentials, which exist just for a single program's needs. Google IAM supports Service Accounts that are not tied to any human. They can be enabled and disabled without impacting individual users.
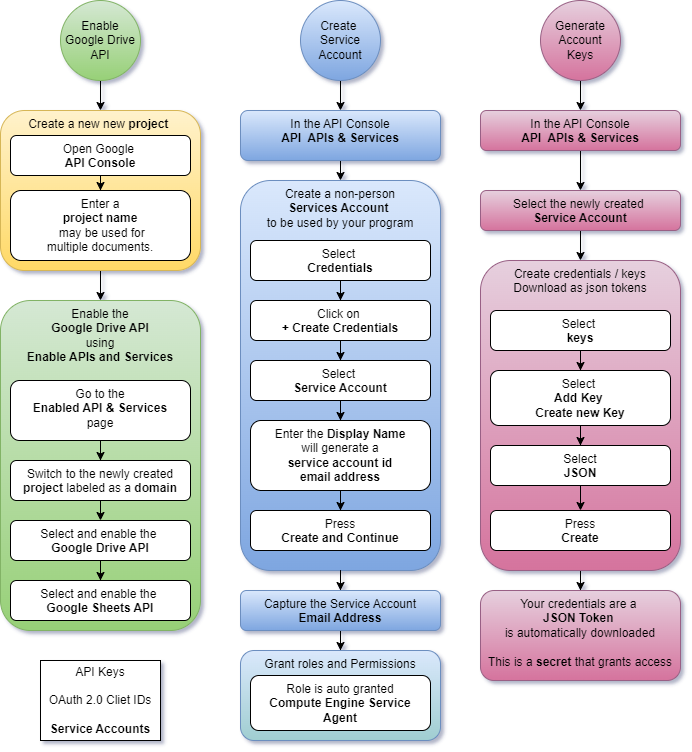
Accessing Google Docs via API means you have to enable Google Drive API in a project, create an identity/credentials for the program, and then give the identity access to the docs or the API. There are plenty of good tutorials that walk you through setting up an account. They are often light on the overall process or how the steps tie together. It can be confusing the first time or 10 you go through it.
- Google services are enabled on a per-project basis. This lets you isolate access and capabilities through judicious project management. Projects are sometimes referred to as domains in the user interface.
- Credentials like Service Accounts, API Keys, or OAuth IDs exist within the scope of a project sometimes referred to as a domain. Credentials/Identities can exist in the root domain or any lower-level domain. Each of these identity types has their own advantages and disadvantages. I mention Service Accounts here because Pysheet and other Python libraries support JSON-based Service Account keys as identity credentials.
- Keys provide a way of authenticating as a Service Account type of Identity when making a request. Google supports JSON and legacy P12 key formats. Libraries can associate these tokens with requests made to Google APIs.
Domain/API/AIM/Account/Document Relationships
I started with the step-by-step because people want to get stuff done. Now we can look at how it all comes together.Detailed Walkthrough
A detailed, screen-by-screen, walkthrough will have to wait for another article. I used this setup guide by Erik Rood targeted at Python pygsheets users when I set up my credentials.







Comments
Post a Comment