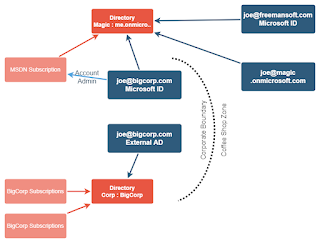
What are we running and how do we know it?

Modern software systems can be complicated with many moving parts. Each of those parts can be updated, upgraded, or changed at any time. We need the ability to understand which versions of each component or configuration are running in each environment at any time. Smart designs, automation, and the appropriate metadata can set us up to understand the specific configurations and versions in each layer in every environment. We will attack this problem in the static / design phases and the dynamic run time phases. What versions do we have available? What versions are we running?